SIEM
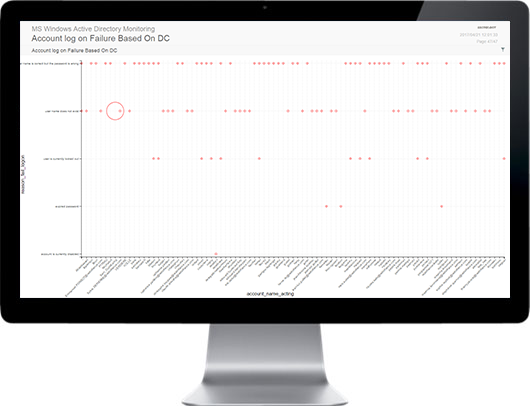
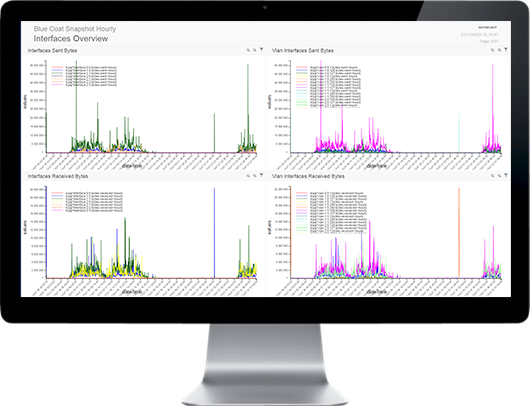
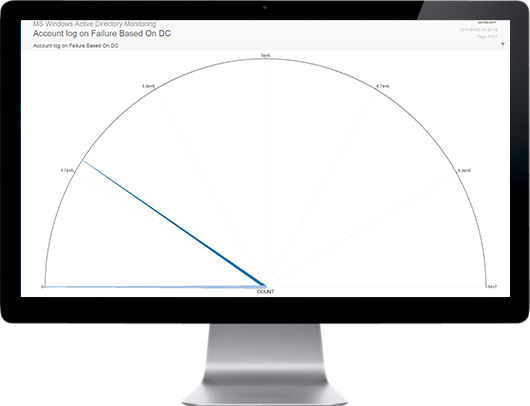
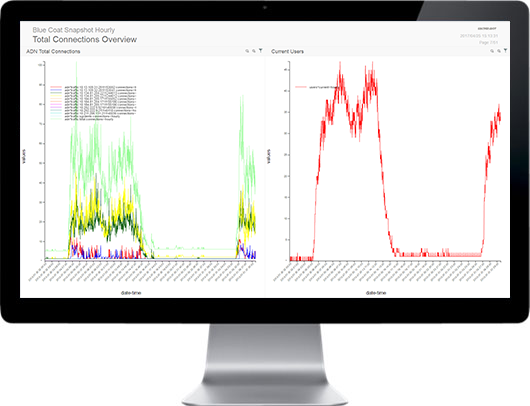
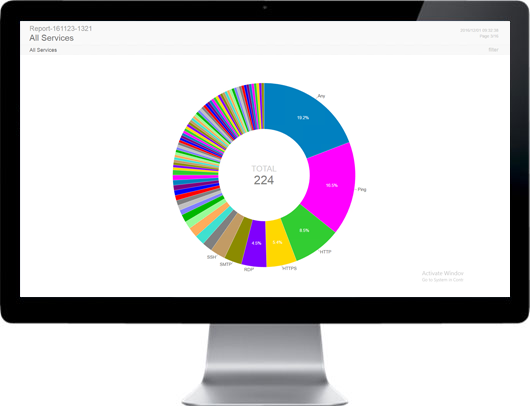
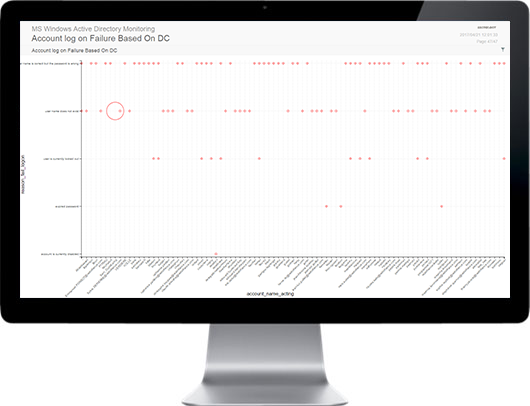
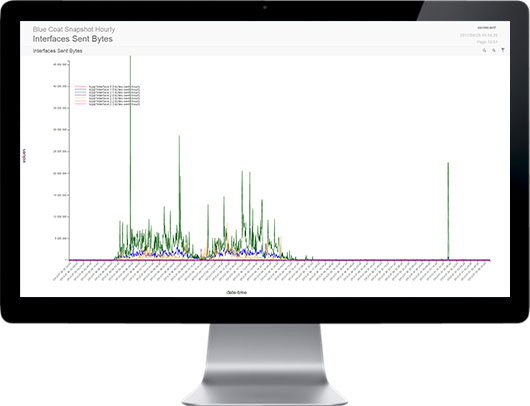
SECNOLOGY combines SIM & SEM to offer a truly unique SIEM solution. It provides real time or on demand analysis of security alerts generated by network & security hardware and applications. The segment of security management that deals with real-time monitoring, correlation of events, notifications and console views is commonly known as security event management (SEM). The second area provides long-term storage as well as analysis and reporting of log data, and is known as security information management (SIM). As with many meanings and definitions of capabilities, evolving requirements continually shape derivatives of SIEM product-categories. With SECNOLOGY no need to turn to big data platforms, such as Hadoop, to complement SIEM capabilities by extending data storage capacity and analytic flexibility: