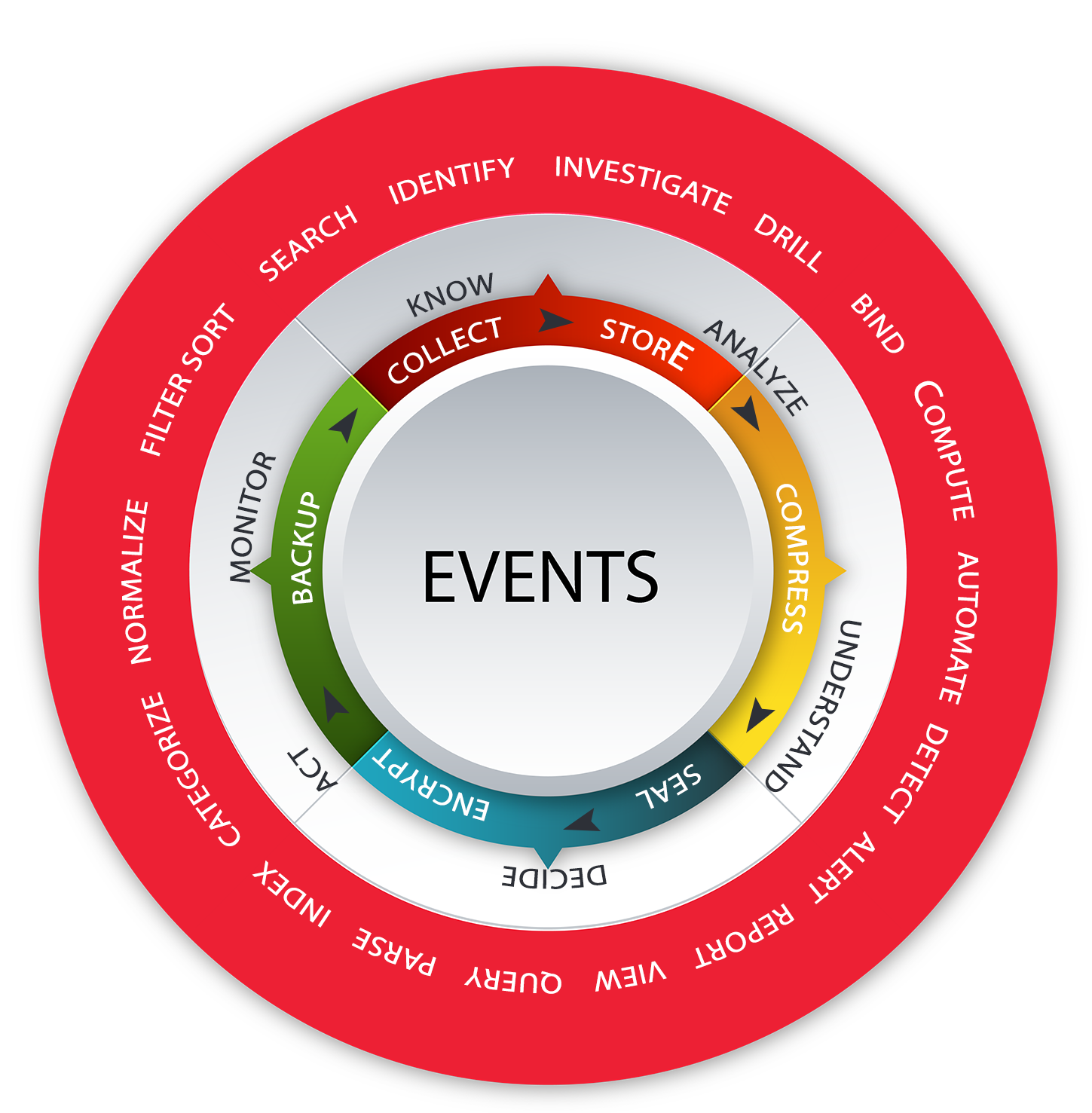
Grid Computing Architecture
Using a flexible Grid Computing Architecture to provide power, scalability and high-availability, SECmanage can process data on many SECmanage systems simultaneously. To process 17 Terabytes a day, simply position multiple SECmanage systems. Leveraging this Architecture, dedicate some SECmanage systems for specific tasks such as reporting, correlating, binding, alerting, archiving, parsing, etc…