Data Governance
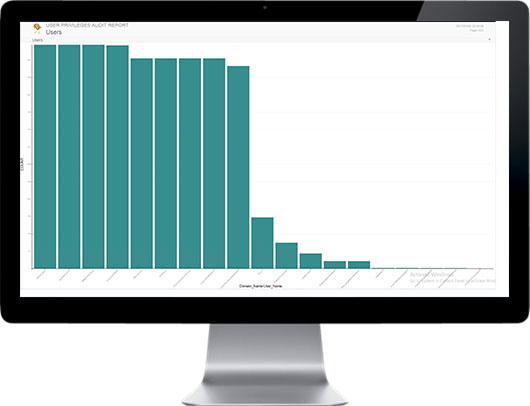
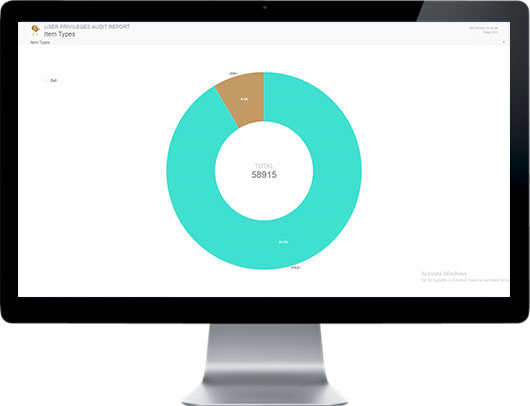
User data access needs change, and access permissions are seldom revoked; users accumulate more and more access authorization over time. Organizations lack the ability to see who is accessing data and what they’ve accessed, identify excessive permissions, and identify data owners.
SECNOLOGY offers a framework to achieve comprehensive data governance. SECNOLOGY aggregates user, permissions, data and access event information from directories and file servers. Apply easy and powerful analytics to show detailed data use and determine rightful access.