How Do I Get continuous Visibility ?
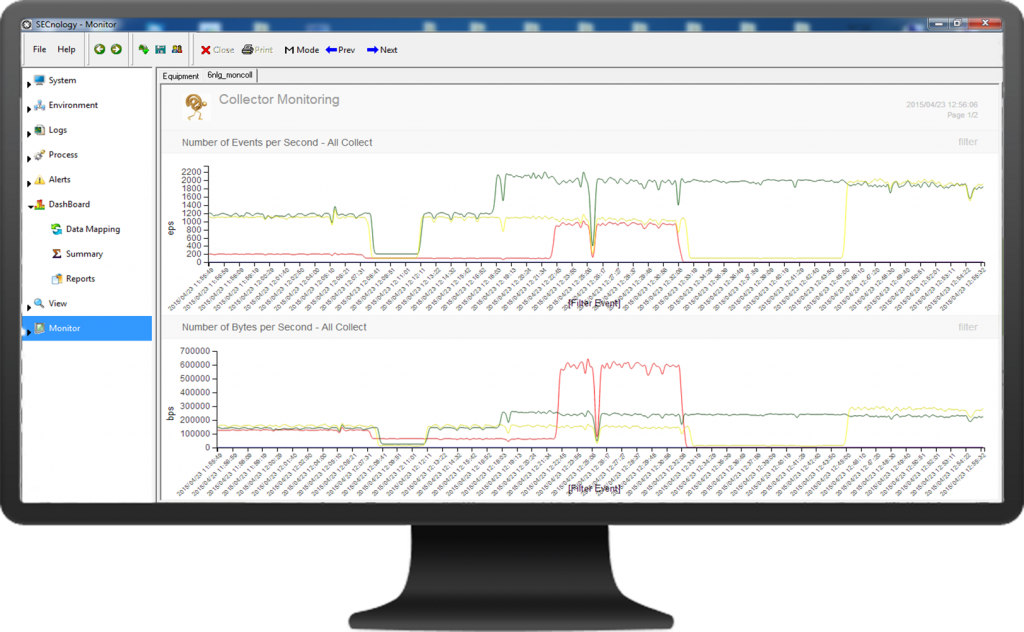
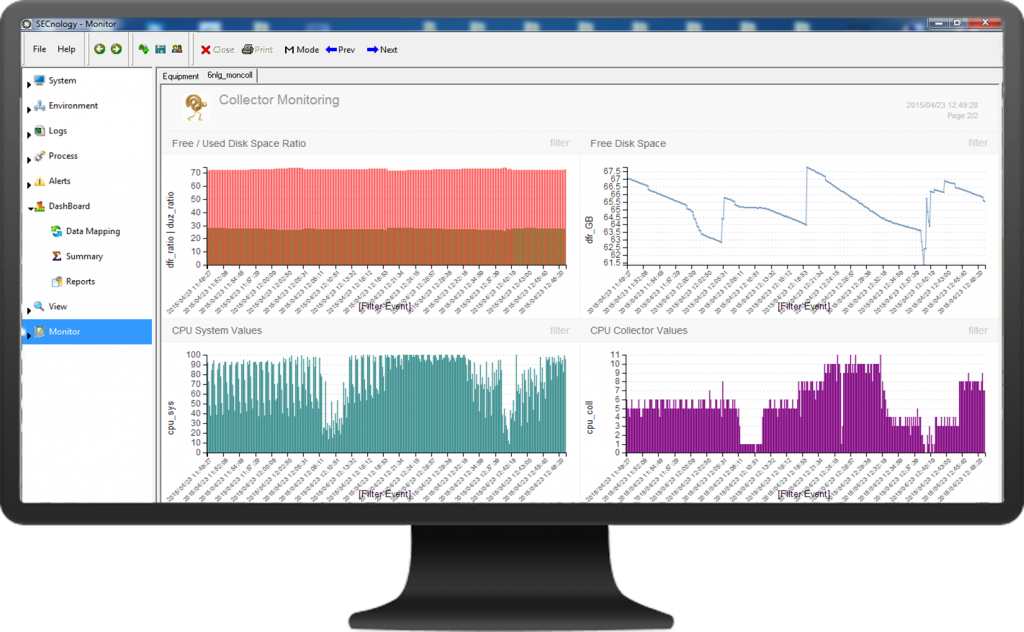
How do I get continuous visibility so i can understand where the vulnerabilties are and take corrective action in a timely Manner?Do you need an answer to this question? SECNOLOGY provides a comprehensive solution to this challenge, and the answer starts here. The first step is to gather network & security events.